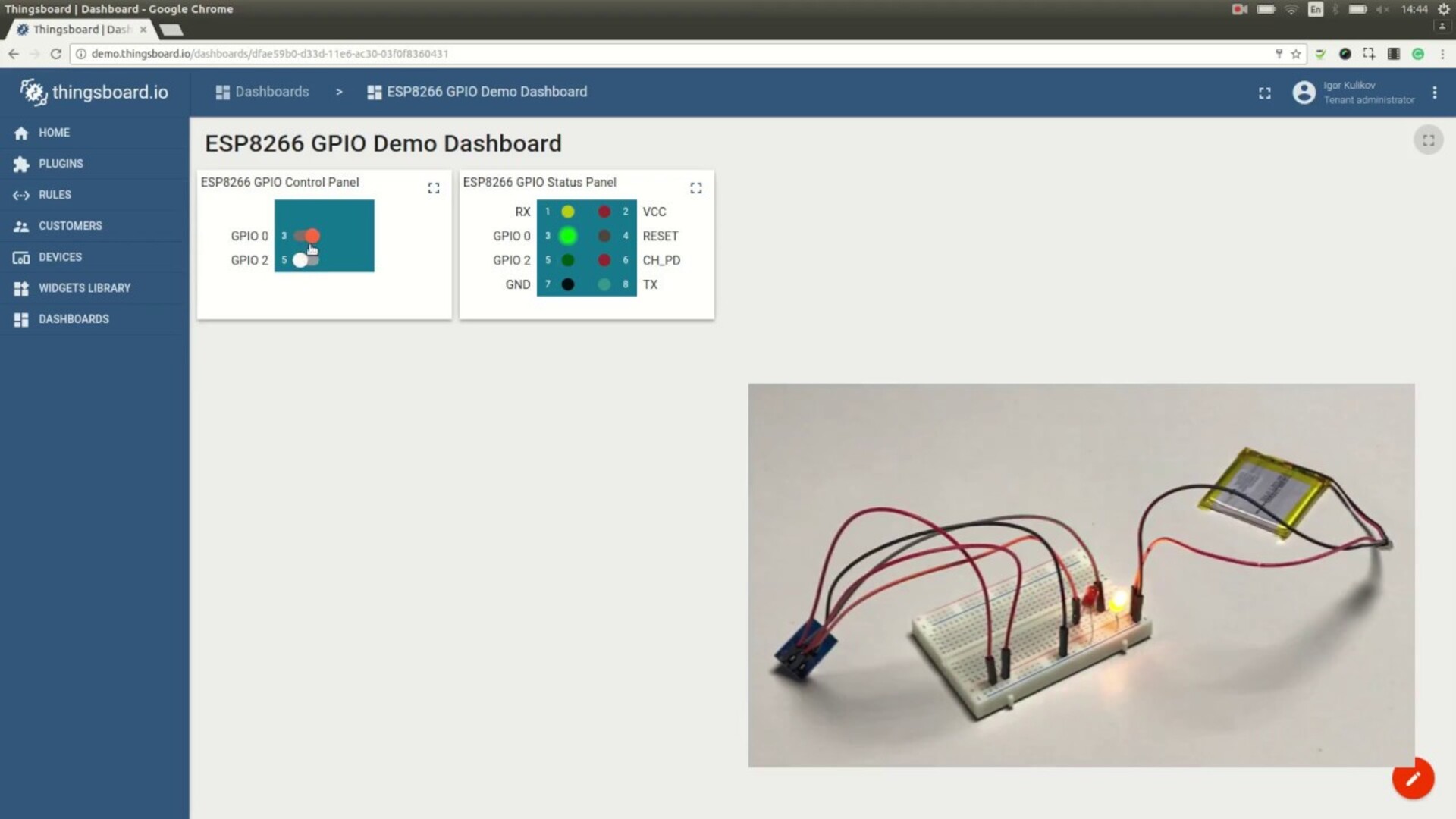
Protect your IoT devices and networks with these essential security practices. From encryption to authentication, we cover it all.
The IoT Security Landscape
As IoT deployments grow exponentially, security vulnerabilities become increasingly critical. A single compromised device can provide attackers access to your entire network. These ten best practices will help you build a robust security posture for your IoT ecosystem.
1. Implement Strong Authentication
Never use default credentials. Each device should have unique, strong authentication:
- Generate unique passwords per device during provisioning
- Implement certificate-based authentication where possible
- Use multi-factor authentication for administrative access
- Rotate credentials regularly and after any security incident
2. Encrypt All Communications
Data in transit must be protected:
- TLS/SSL: Use TLS 1.2 or higher for all network communications
- End-to-End Encryption: Implement application-level encryption for sensitive data
- Certificate Validation: Always validate server certificates to prevent MITM attacks
- Hardware Security Modules: Store encryption keys in secure hardware elements
3. Secure Device Provisioning
The initial setup is critical:
- Use secure boot to ensure only trusted firmware runs on devices
- Implement zero-touch provisioning with device attestation
- Generate unique device identities during manufacturing
- Validate device authenticity before allowing network access
4. Regular Firmware Updates
Keep devices patched and up-to-date:
- Implement OTA (Over-The-Air) update capabilities
- Digitally sign firmware images to prevent tampering
- Establish a rollback mechanism for failed updates
- Monitor for security vulnerabilities and patch promptly
- Test updates thoroughly before wide deployment
5. Network Segmentation
Isolate IoT devices from critical systems:
- Create dedicated VLANs for IoT devices
- Implement firewall rules to restrict device communication
- Use network access control (NAC) to enforce security policies
- Monitor network traffic for anomalous behavior
6. Minimal Data Collection
Follow privacy-by-design principles:
- Collect only data necessary for device functionality
- Implement data minimization and anonymization
- Establish clear data retention and deletion policies
- Comply with GDPR, CCPA, and other privacy regulations
7. Secure APIs and Interfaces
Protect all access points:
- Implement OAuth 2.0 or similar for API authentication
- Use rate limiting to prevent abuse
- Validate all inputs to prevent injection attacks
- Keep APIs versioned and document breaking changes
- Implement comprehensive logging for security audits
8. Physical Security
Don't neglect physical access:
- Use tamper-evident enclosures for deployed devices
- Disable unnecessary ports and interfaces
- Implement secure element chips for key storage
- Erase sensitive data if tampering is detected
9. Continuous Monitoring
Detect and respond to threats quickly:
- Implement centralized logging and SIEM integration
- Monitor device behavior for anomalies
- Set up automated alerts for security events
- Conduct regular security audits and penetration testing
- Maintain an incident response plan
10. Supply Chain Security
Verify the entire chain of custody:
- Vet third-party components and suppliers
- Verify software dependencies for known vulnerabilities
- Implement secure manufacturing processes
- Maintain a software bill of materials (SBOM)
- Establish supplier security requirements in contracts
Conclusion
IoT security requires a multi-layered approach. By implementing these ten best practices, you'll significantly reduce your attack surface and protect your IoT ecosystem. Remember: security is not a one-time effort but an ongoing process that must evolve with emerging threats.
Michael Roberts
Expert IoT consultant and technical writer with years of experience in industrial automation and smart systems.